Navigating the May 2019 Security Patches for SQL Server Deployments
This past week has been a doozy for security updates. There have been quite a few security alerts and patches. In this post, I’ll guide you through them as they relate to SQL Server and the operating systems that it runs on.
More Intel Processor Woes – Side-Channel Vulnerability/Microarchitectural Data Sampling (MDS)
After Spectre and Meltdown a few months back (which I cover in this blog post from January 4), another round of processor issues has hit the chipmaker. This one is for MDS (also known as a ZombieLoad) This one comprises the following security issues: CVE-2019-11091, CVE-2018-12126, CVE-2018-12127, and CVE-2018-12130. Whew! Fun fact: CVE stands for “Common Vulnerabilities and Exposures”.
As of now, this is only known to be an Intel, not AMD, issue. That is an important distinction here. The official Intel page on this issue can be found at this link. This issue does not exist in select 8th and 9th generation Intel Core processors as well as the 2nd generation Xeon Scalable processor family. (read: the latest stuff) This link in the Intel page is the detailed processor family list and what is/is not affected. If there are hardware-level fixes, those would come from your vendors such as Cisco, Dell, and HP. Many OSes as well as SQL Server have issued statements, guidance, and/or patches for this new Intel processor flaw.
Below is everything that relates to SQL Server or your underlying server configurations. Oh, and patch your systems RIGHT NOW.
Hyperthreading (Processor-level)
This is the biggie. If you look at most of the mitigations beyond patching, nearly everyone is, depending on the circumstance, recommending disabling hyperthreading (HT) on the physical processors. Guidance will vary from vendor to vendor. Doing this will require downtime as you will need to boot into BIOS/UEFI to do this. It will most likely impact performance if you were relying on HT, so check your SQL Server workloads. Before disabling HT, check the guidance from your vendors.
SQL Server
The Spectre/Meltdown KB article (4073225) was updated to include this new flaw. SQL Server does not require any specific patches for MDS. Please see the Windows Server section and specifically ADV190013 (linked below) for Microsoft’s full view on this.
Red Hat Enterprise Linux (RHEL)
SQL Server is currently supported on RHEL 7.3, 7.4, and 7.6. Red Hat did an excellent page explaining things which even has a video on how the attack could work. Even if you don’t use RHEL, the video is a good watch. Their specific vulnerability page for this new flaw can be found here. Read it, but if you want to skip to the conclusion, switch to the Resolve tab.
SUSE Linux Enterprise Server (SLES)
SQL Server is supported on SLES 12 SP2.
Here are their specific pages for each of the vulnerabilities and how to deal with them:
Ubuntu
SQL Server is supported on Ubuntu 16.04 which has a patch for MDS (the plain English stuff). The specificl Ubuntu Knowledge Base article for MDS can be found here which covers any updates that are needed.
VMware
VMware published a security advisory (VMSA-2019-0008) for the MDS issue. They cover all the versions affected and most importantly, which versions are the fixed ones. The main VMware Knowledge Base article linked you should be concerned with is KB67577. That article covers HT.
Windows Server
Microsoft updated their KB article on side-channel vulnerabilities (4072698) to include MDS. It has two very specific links: ADV190013 and KB4457591. Microsoft also has information for Azure IaaS VMs. I would read both carefully as they talk about the potential impact to performance. KB4457591 has a great section on whether or not you would need to disable HT, especially as it relates to Hyper-V.
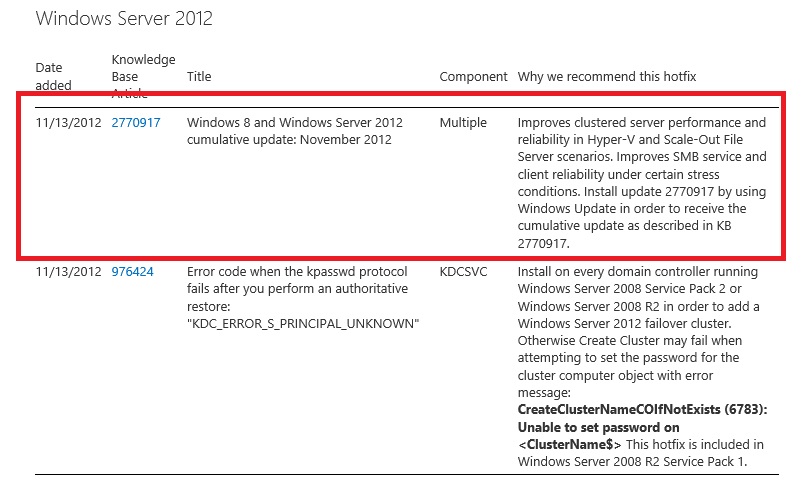
From a fix perspective, the good news is that Microsoft shipped patches as part of the latest OS update released for Patch Tuesday covering Windows Server 2008, 2008 R2, 2012, 2016, and 2019. The link to the respective software is found at the bottom of ADV190013.
Amazon Web Services
AWS also had to deal with this flaw. Their information can be found in Security Bulletin AWS-2019-004. If you are using their IaaS services (EC2), you will have to check your IaaS VMs running in Google Compute Engine to make sure they are patched and that they are not running untrusted workloads.
Google Cloud Platform
Like AWS and Azure, GCP has this problem, too. Similar to AWS (and Azure), the hosts were taken care of according to their posted notice. You will have to check your IaaS VMs running in Google Compute Engine to make sure they are patched and that they are not running untrusted workloads.
Remode Code Execution Vulnerability in Remote Desktop Services (Terminal Services)
On May 14, Microsoft published security bulletin CVE-2019-0708 which details how a worm could happen with older versions of Windows desktop and server with Remote Desktop Services. The security bulletin describes how it would work, and what is – and is not – vulnerable. The good news is that if you are running Windows 8, 8.1, or 10 for the desktop or Windows Server 2012, 2012 R2, 2016, or 2019, you are safe. However, If your SQL Server instances are running on Windows 7 or Windows Server 2003, 2008, and 2008 R2 you are not. This one is bad enough that Microsoft patched Windows 7 and Windows Server 2003 which are out of support. While we do not see much Windows Server 2003 at our customers, there is a fair amount of Windows Server 2008 and 2008 R2 out there. The last version that was supported by Windows Server 2008 R2 was SQL Server 2014.
The security patches for Windows Server 2008 and 2008 R2 can be downloaded from this link. Note that this also affects Itanium processors if you still have those.
The security patch for WIndows Server 2003 can be downloaded from this link.
SQL Server 2017 – SQL Server Analysis Services
SQL Server released a rare security patch recently for SQL Server Analysis Services. According to KB4497700, There is a potential leak of restricted data that is not protected correctly by the Object-Level Security (OLS) system. This does not affect any other version of Analysis Services other than 2017, and is fixed in a GDR for RTM if you have not applied any CUs and a security update for CU14 (CU14 + GDR). CU14 is a re-release from March 25.
Other Stuff
There have been fixes to other things such as Adobe Flash, Internet Explorer, and more. I’ve coverd the major things, but anything that ships as part of the underlying OS is important to patch if it’s installed.
Call To Action
Security flaws need to be patched right away. Yes, that means downtime you probably didn’t plan, but do you want to be the next company to land in the headlines because you didn’t patch? We would be happy to help you figure out the right patching strategy and help you migrate to later platforms/versions that are more secure. Contact us today.
We have an upcoming webinar on June 5 Why Upgrades Matter where we will discuss the reasons you should do your best to stay up to date with releases and patching since there can be benefits, too. Read the abstract here and register today.